What is Data Security?
Data Security safeguards digital data from unwanted access, corruption, or theft. It is a notion that imparts physical security to hardware and software devices and covers all aspects of information security. It also imparts administrative and access controls and logical security to software applications. It also covers policies and procedures to be followed by a company.
Why is Data Security important?
Data is a valuable asset that generates, acquires, saves, and exchanges for any company. Protecting it from internal or external corruption and illegal access protects a company from financial loss, reputational harm, consumer trust degradation, and brand erosion. Furthermore, regulations for securing data, imposed by the government and the industry, make it critical for a company to achieve and maintain compliance wherever it does business.
Main elements of Data Security
The three components of Data Security that all companies should adhere to are confidentiality, integrity, and availability. The CIA triad is a security paradigm and framework for the protection of data. Here is what each fundamental piece implies in terms of preventing unwanted access and data exfiltration.
- Confidentiality: Ensures that only authorized users, with appropriate credentials, have access to data.
- Integrity: Ensures that all data is accurate, trustworthy, and not prone to unjustified changes.
- Availability: Ensures that data is accessible and available for ongoing business needs in a timely and secure manner.
Aftermath of Data Breach
The immediate effects of a data breach are less known, yet they may be costly to a business. In the aftermath of a data breach, companies often face a slew of immediate financial consequences. A data breach may result in penalties from the Payment Card Industry Security Standards Council. An additional fine may be imposed by regulatory authorities and card network brands, depending on the circumstances.
Forensic investigations are a type of forensic inquiry. One of the implications of a data breach is that a company is accountable for conducting a forensic investigation to establish the cause of the data breach. These investigations frequently produce evidence and insights that might aid in the prevention of future data breaches.
Businesses that suffer a data breach may have to pay for credit monitoring for consumers whose information has been exposed. Remediation activities have to be done, which include card replacement costs, identity theft repair, and more compliance requirements. Hence, the importance of data security is clear.
Types Of Data Security Controls
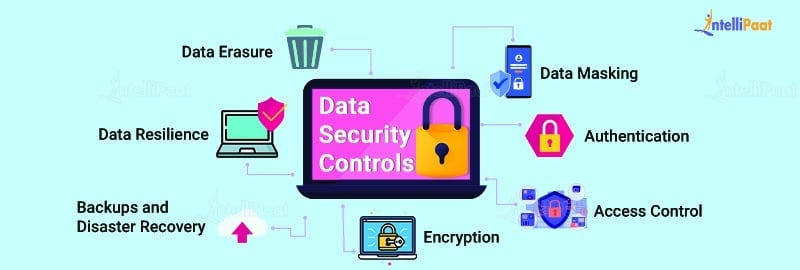
The below-mentioned control measures have to be followed for securing data and avoiding data breach.
Access Control
Limiting both physical and digital access to central systems and data is an example of a strategy for securing data. It involves ensuring that all computers and gadgets are password-protected and that physical places are only accessible to authorized employees.
Authentication
Provide authentication measures, such as access restrictions and correct identification of people, before giving access to data. Passwords, PINs, security tokens, swipe cards, and biometrics are common examples.
Backups and Disaster Recovery
Good security means you have a strategy in place to safely access data in case of a system failure, disaster, data corruption, or breach. To restore, you will need a backup data copy kept on a distinct format such as a hard drive, local network, or Cloud.
Data Erasure
Appropriate discarding of data regularly is necessary. Data erasure is more secure than ordinary data wiping since data erasure uses software to wipe data completely on any storage device. Data erasure ensures that data cannot be recovered and, hence, will not fall into the wrong hands.
Data Masking
Data masking software obscures letters and numbers with proxy characters, concealing information. Even if a person obtains access to data illegally, it is successfully masked. Only when an authorized user acquires data, then does it revert back to its original state.
Data Resilience
With comprehensive security, you can withstand or recover from failures. Avoid power outages and mitigate natural catastrophes as these factors can breach data protection. Data privacy can be implemented by incorporating resilience into your hardware and software.
Encryption
With the help of encryption keys, a computer algorithm converts text characters into an unreadable format. The content can only be unlocked and accessed by authorized people who have the appropriate keys. To some extent, everything from files and databases to email conversations should be secured.





